[4 min read]
Data ownership is a complicated topic, much more complicated than most might think. We often talk about data security in possessive terms of “my sensitive data”, “my health information” or “my Personal Identifiable Information (PII)”, but what does ownership of that data actually mean? There are likely countless copies of that data in many locations, ranging from your doctor's office and bank to your gym membership.
Do you own every copy, or does the organization hosting the data own it? For that matter, do you even know where all “your” data is? Who really owns data, where it is stored, and who has the right to access it is far from straightforward.
Handling employee and customer data requires security executives to understand what data is being stored, how it is being used, and who has access to it. More than ever, organizations must demonstrate proper data handling in order to stay compliant with an increasing number of security regulations.
Data ownership can be tricky
A KMPG survey found that 87 percent of Americans believe that data privacy is a human right and 54 percent don’t trust companies to use personal data in an ethical way, but as mentioned, data ownership is far from straightforward. For example, I use a Garmin watch to track my exercise goals daily. When I see my personal information on my Garmin application, who owns that data? The watch shows how far I’ve walked, how many steps I’ve taken, my heart rate, and more. One might conclude that this data is mine since it is about me. However, would I have that data if I wasn’t using the Garmin watch? Garmin is doing the monitoring and measuring, counting my distance, speed, and location, so do they have an argument to say it is their technology enabling the collection of data, and the data would not exist without their product? Can they claim it is actually their data?
 Do I own the data on my smartwatch?
Do I own the data on my smartwatch?
Let’s take the example further. I run the Garmin app on my IoS smartphone. Does Apple then have a claim to the data? After all, without their operating system, I would not be able to visualize the information. What seemed like an easy data ownership question now has lots of possibilities. So how do we define data ownership in a way that satisfies all parties?
[Read more: Embracing a Data-Driven Approach to Risk Management is the Key to Success]
Data Security: Rights of Use
Avoid the contentious concept of ownership, and focus on data rights instead. When we think about how we want data to be used, rather than who owns it, it becomes easier to set parameters around different use cases. Following our earlier example, an individual should have domain over their own personally identifiable information (PII) but Garmin should have the right to use the information generated by their proprietary technology. Garmin might want to aggregate user information for product development purposes or Apple may use underlying application usage information for their business trends. There are many use cases where all parties benefit from a collaborative approach to sharing information.
Rather than trying to define data ownership, we need the appropriate guardrails set around each individual’s right of use. By doing so, we avoid the more emotive issue of thinking of data as property and instead focus on how the data is used and by whom. This is primarily how data privacy laws and regulations think about data, making it clear that data custodians must set clear rules for how they will use a customer's data. When companies violate these data rights they can fall foul of legislation. One recent data rights example is where Meta is being sued by the State of Texas. Texas claims the company collected facial recognition data without customer consent, shared it with third parties, and did not destroy the information in a timely manner — all in violation of state law.
An Explosion of Privacy regulations
Texas is not the only government entity being more active here. According to IAPP, there were 50 new privacy legislation bills introduced in the US between 2019 to 2021. This follows the enactment of GDPR in Europe and CCPA in California. These laws set out an individual's right of use in accordance with the service provided that enables the creation of the data. For example, when I sign the Garmin terms of use, Garmin is legally required to explain how it will use the information it collects and is then required to use the data only as it has outlined.
This is why it Is important to read those terms of use, rather than just accept them as we all tend to do. There is a risk in your relationship with all companies that hold customer data. For example, in 2019 Facebook was fined $5 billion by the FTC for misusing customer data and was forced to improve its data security program. Organizations must protect the data in line with industry standards and legislation. Many companies are turning to industry standards such as SOC 2, HITRUST, and NIST in order to demonstrate to customers and vendors that they are operating with the highest levels of data protection in mind. Organizations can use SOC 2 certification as a competitive advantage to demonstrate the degree to which they consider data security and compliance seriously and that they are protecting the data to which they are privy.
Integrated risk management tools you can leverage to track data
Many organizations leverage integrated risk management solutions, such as the Ostendio MyVCM platform to manage their data security programs. These solutions enable organizations to know what data they have, where it is located, and who has access to it, thereby streamlining the task of these data security rights rules. With these solutions, organizations can track data and operate in line with various regulations and standards and be confident in their ability to manage and handle data appropriately.
There’s no doubt that data breaches are on the rise and knowing where your data is and who has access to it is the first step in your data security program. Talk to the experts at Ostendio to learn more about how the MyVCM platform could help you track your data and start your compliance journey.
.png?width=498&name=Who%20owns%20your%20data%20blog%20post%20(1).png)

February 23, 2022
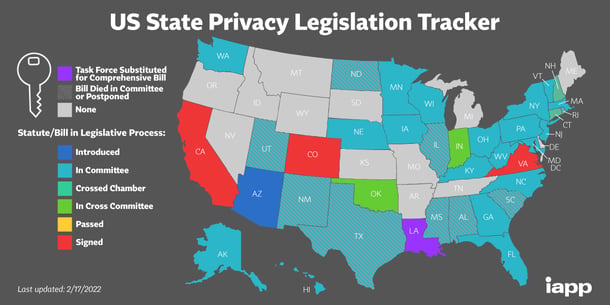 Source: IAPP
Source: IAPP
Comments