If you aren’t familiar with the Secure Controls Framework (SCF), you should be. It’s a non-profit organization dedicated to providing content that helps organizations navigate the security and compliance maze. Right now they are rolling out the ‘Security & Privacy Capability Maturity Model’ (SP-CMM). It’s designed to give organizations an objective way to evaluate the maturity of their security and privacy program.
In simple terms, it rates organizations along a 6 point scale called a Capability Maturity Model. From the SCF website, the levels of Maturity are:
- CMM 0 – Not Performed
- CMM 1 – Performed Informally
- CMM 2 – Planned & Tracked
- CMM 3 – Well-Defined
- CMM 4 – Quantitatively Controlled
- CMM 5 – Continuously Improving
These 6 levels are plotted against two axes: Cost & Complexity, and Maturity level (people, processes & technology).
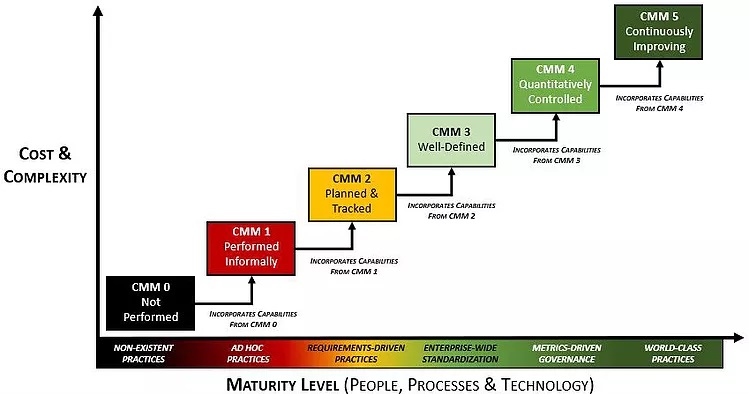
Source: Secure Controls Framework
While different Capability Maturity Models have been around since the 1980’s, there is a lot to appreciate in this version, not least of which are the multiple dimensions and the breadth of applicability. Indeed we think this version should be used as a measuring stick for companies of all shapes and sizes, and we will be writing a lot about it in the near future.
But let’s start with one of the first questions people have asked about this: “I’m a small/medium/large company, so where should I expect to fall on the scale?” This is not a simple question to answer, but the framework does a great job of describing what your IT organization probably looks like based on company size and maturity level.
The table below summarizes the typical IT function for Small, Medium and Large Organizations at each of the 5 levels of the CMM Framework.
| CMM Level |
Small Organizations |
Medium Organizations |
Large Organizations |
|---|---|---|---|
|
CMM 0 |
Negligent: No Processes or practices. Common in startups but creates major risk. |
Unrealistic scenario. Medium and Large organizations cannot function without some kind of dedicated security function and knowledge of relevant controls. |
|
|
CMM 1 |
No IT or outsourced IT function with "Break/Fix" approach to security. |
In-house IT but no focus on security or compliance to relevant controls. |
|
|
CMM 2 Planned & Tracked |
"Side of Desk" - Clear requirements but no staff members dedicated to privacy & security. |
Dedicated cyber (privacy & security) person or team with documented requirements. |
|
|
CMM 3 |
Small IT staff, clear requirements; leader with some cyber experience. |
Cyber-focused members of the IT team; clear requirements; leader with strong cyber background. |
|
|
CMM 4 |
Unrealistic to attain. Small organizations do not have the budget or staff to achieve Level 4 compliance. |
Specialized Privacy and Security specialists within the Cyber part of IT team; Competent senior leader (e.g., CISO); Metrics-driven with transparency across the organization. |
|
|
CMM 5 |
Unrealistic to attain. Small and medium organizations do not have the budget or staff to achieve Level 5 compliance. |
CISO-led team with cyber specialists; Business-wide and board-level visibility into key metrics; cyber practices part of core business strategy. | |
There is a lot that jumps out from the table above, but one part in particular is operating at CMM 0 or CMM 1 levels may be considered to be ‘negligent’. The rationale the SP-CMM provides is that “if a control is reasonably-expected to exist, by only implementing ad-hoc practices in performing the control that could be considered negligent behavior.”
If you are thinking "my company falls in the negligent box, what should I do?" Don't panic.
There is clearly not a one-size fits-all model, and just because your IT team looks like something described in the table above, it doesn’t necessarily mean your organization is at that particular CMM level. If you are looking for a way to evaluate your security program the Ostendio MyVCM platform can show you exactly where you are, and where you are going; let us know if you’d like to discuss how the CMM applies to your business or see a MyVCM Demo.
Tags:
Cybersecurity, Data Breaches & Data Privacy, Integrated Risk Management, Risk Management & Compliance
August 29, 2019

Comments