[5 min read]
To the busy CISO, it might seem like implementing a GRC (Governance, Risk and Compliance) tool will be an easy way to create and manage a data security and risk management program. However, upon implementation, CISOs soon realize that a traditional GRC tool is not enough for today’s complex business environment. The good news is that there is an increasing array of alternatives to GRC tools (or GRC software) that more effectively enable companies to build a culture of security, making it easier to complete complex security audits such as SOC 2, FedRAMP, and HITRUST.
According to Gartner, GRC “enables the simplification, automation, and integration of enterprise, operational, and IT risk management processes and data.” While this is a great goal, most GRC tools fall short of what a business really needs when building an effective data security program.
[Read more: The evolving landscape of Integrated Risk Management]
When considering a GRC tool, take the time to evaluate the needs and the benefits to your company.
- - Where are you currently in your security journey and where do you want to be in the future?
- - Are you about to apply for a certification or conform to a specific industry regulation?
- - Who on your team is going to champion the use of the GRC tool and integrate its use into your organization?
.png?width=669&name=twitter%20size%207%20reasons%20GRC%20tool%20not%20enough%20(1).png)
The 7 limitations of a traditional GRC tool
There are many limitations of a traditional GRC tool and that is why organizations are now moving to IRM tools to integrate data security and risk management into their whole business.
Here are 7 limitations of a traditional GRC tool and why IRM is better:
1. GRC tools are only used by a few employees within the organization
While GRC tools are limited to a select number of employees, the most successful data security and risk management programs involve the entire organization from the most junior employee to the CEO. We have learned over time that data security is the responsibility of the entire organization, and in order to protect hackers from accessing sensitive information stored on your corporate system, everyone needs to be involved. An IRM tool, by contrast, empowers all team members to enhance the security posture of the organization. Training is trackable and can be set up for regular intervals to make sure everyone remains up to date on the latest security threats and how to avoid them.
2. GRC tools rely on information from third-party sources and are typically updated manually
In this fast-paced environment, manual operations are no longer acceptable for data collection and use. GRC tools are limited because they are not using real-time data. Alternatively, IRM tools enable access to data in real-time.
3. GRC processes are secondary, and so are often not a priority
GRC tools are limited since the processes are typically secondary and an incremental effort above and beyond the work of the company. Like any secondary process, it gets deprioritized which, in turn, affects the accuracy of the information. The reason GRC tools are considered secondary is the information they contain is incomplete, inaccurate, and out of date, and the overhead to reverse this is typically above what an organization would reasonably spend. IRM tools are integrated into the overall operational processes of the organization and work in conjunction with all departments to deliver security that’s always on, always secure, and always auditable.
4. GRC tools are inflexible when new standards are introduced
New standards and regulations are constantly evolving. GRC tools often lack the ability to stay current with the evolving changes. IRM platforms, like MyVCM, provide access to over 125 standards and regulations within the platform. Prior to implementing an IRM tool, make sure that the provider enables a crosswalk functionality to enable the evidence collected for the question on one standard to be used for similar questions on a different standard, to reduce the time of preparing and completing multiple security audits.
5. GRC tools don’t provide robust risk monitoring and analytics
Today’s business users and auditors demand real-time insight into risk and compliance status. GRC tools fail to combine high-level health and progress indicators with granular details into issues that need attention. This means a lack of visibility into how risks have been resolved. Look for an IRM platform that offers visibility with real-time data to make more informed decisions based on the most up-to-date information.
6. GRC tools do not allow for collaboration with your auditor
GRC platforms are an “internal-only” black box. Auditors typically do not have direct access to any of the evidence collected. In order to complete an audit, you will need to export data to a dropbox or share it in a spreadsheet. By using an IRM platform, companies can treat their auditor as part of the team and ensure that they can use the same technology for a synchronized view of compliance. By using the right IRM platform, companies can communicate within the platform directly with their auditor and collaborate around documentation and evidence. This ensures that the auditor always sees the most up-to-date evidence available and simplifies the tracking of version control.
7. GRC tools don’t link with your vendors to show their security posture
The majority of security breaches are the result of lax vendor management. Traditional GRC tools do not extend beyond the organization to third-party vendors, and therefore enable little control over the compliance with business partners. An effective IRM platform will allow you to send your vendors a customized security assessment to ensure that they are also protecting any of your company data that they have access to.
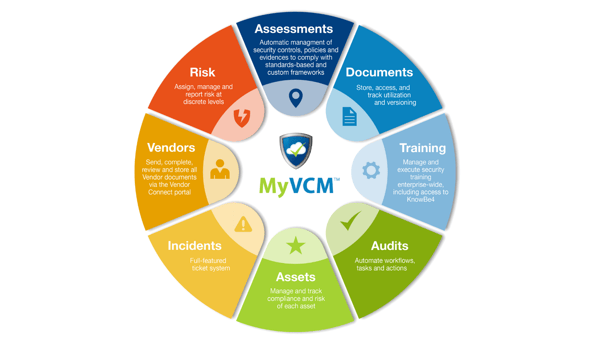
Image: The features of the MyVCM platform. Ostendio MyVCM is a single, integrated Cybersecurity and Risk Management platform that works in conjunction with all business operations to deliver perpetual security that's always on, always secure, and always auditable.
What do analysts say?
Gartner’s recent publication, Competitive Landscape: Integrated Risk Management Report, attempts to evaluate which platform would be the best solution for customers. It describes Ostendio MyVCM as “innovative” in this space. In the report, Gartner recognizes the Ostendio MyVCM Trust Network for creating a network effect that improves transparency and efficiency for all participants, across multiple security frameworks, including SOC 2.
Learn more about Integrated Risk Management
Ostendio has been helping customers build, operate, and showcase their data security and risk management programs since 2014. By understanding the limitations of a traditional GRC tool, CISOs instead make the move to IRM for a solution that can grow with their business.
The Ostendio MyVCM platform helps companies comply with over 125 standards and regulations globally, and we make the move to an IRM tool a simple process. Our Professional Services team helps many customers who need extra assistance or guidance when preparing for a complex data security audit. Check out our Platform Overview or Request a Demo today to see how Ostendio can help your business.
Tags:
SOC 2, Cybersecurity, Integrated Risk Management, Risk Management & Compliance, audit, security audit
May 10, 2022
.png?width=594&name=Free%20GRC%20tool%20twitter%20(2).png)

Comments