Data breaches aren’t just a problem for security professionals. The impact is felt across the whole business—from your legal team, embroiled in litigation, to your frontline employees, who can’t access the tools they need to do their jobs. Everyone needs to play their part in managing the risks, as well as staying compliant with ever-changing security and privacy regulations.
Security and compliance regulations and requirements differ by state, country, and industry - making it difficult for organizations to stay compliant. New privacy mandates such as the EU's General Data Protection Regulation, the California Consumer Privacy Act and the Data Security and Breach Notification Act can make it hard to wrap your head around all the myriad of changes.
Fines for non-compliance are also becoming increasingly larger – for example, if a firm infringes on several GDPR provision, on the upper end, the company can be fined 4% of annual revenue or $24 million (whichever is GREATER!) How much could non-compliance cost you? It’s imperative that you make security and compliance a part of your daily business operations. How can you align your cybersecurity and compliance efforts?
1. Evaluate your Risk (and your Vendors)
The threat environment is constantly evolving. Conducting an annual risk assessment to understand your threat environment will give you a benchmark to measure against - after all - you can’t manage what you can’t measure.
Once you understand your risk profile, you also need to consider the threat third-party services pose. The infamous Target data breach is just one example of the threat 3rd party vendors pose. Target was hacked when their HVAC vendors credentials were stolen. Think about who you let have access to your systems – do they REALLY need it to perform their jobs adequately?
Security is a journey, not a destination. You will never be 100% secure but by understanding your risks, and remediating them, you will be in a much better position to thwart attacks.
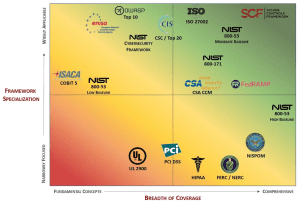
2. Choose Your Framework
Understanding your risk profile will help you to choose a framework to map to. Some things you should consider before selecting your framework:
• Scope of coverage (breath)
• Amount of details provided (depth)
• Taxonomy (overall arrangement of requirements & formatting)
• Industry-specific terminology
Every company has a unique environment. A framework should be a benchmark and not the ceiling. Each framework has pros and cons – you need to decide what’s important for your organization and its security and compliance goals
The Secure Controls Framework (SCF) is a free resource for businesses needing cybersecurity and privacy controls. The SCFR is a comprehensive catalog of controls that is designed to enable companies to design, build and maintain secure processes, systems, and applications.![]()
![]()
3. Set Up A Formal Compliance Program
After you’ve selected the framework you want to map to, it’s time to set up or align your compliance program. If you’re struggling with where to start, Ostendio’s MyVCM maps to over 100 standards and regulations, allowing you to quickly identify and remediate gaps. 
Like selecting a framework, there is no ‘one-size-fits-all compliance program. An effective compliance program is designed to:
- Communicate your company’s standards and procedures
- Educate and train your employees
- Provide high-level insight
- Audit and monitor systems to see that they are working correctly
- Report on policies, processes, and procedures
Not having a formal compliance program in place can mean countless hours spent getting ready for an internal or external audit.
4. Automate Compliance Processes
With each new wave of threats and breach disclosures, there is a flood of expanded industry standards and compliance regulations.
Automation tools can help organizations manage complex compliance requirements across multiple regulations, standards, and frameworks. Dashboard summaries can provide an enterprise view of your security and compliance program. And automation can give everyone time back in their day: no more manual spreadsheets!
Automating security and compliance processes, and making them a part of your business-as-usual operations removes the ‘boom-or-bust’ approach to audits and security questionnaires.
5. Don’t Operate in a Silo
Information security and compliance is everyone’s role.
Everyone, in every department, should understand the role they play protecting sensitive data.
Conduct frequent security awareness training e.g. phishing simulations, drop USB keys with malware on them etc. IT Security Professionals and Compliance Management must partner to successfully plan for, respond to, and recover from security incidents.
Conclusion
Cybersecurity and compliance is an on-going process which involves the entire organization. Barriers which prevent communication, and cause silos, need to be removed. The increasing weight of new legislation from regulators, coupled with the increasingly diverse risks to which firms are exposed, means that companies need to ensure that no risks fall between the cracks.
An effective compliance program can be used to drive a robust cyber risk management process.
Everyone plays a role in preventing and responding to cyber incidents – does your current compliance program help or hinder this?
Not sure how to get started? Contact us today for a complimentary consultation with one of Ostendio’s security and compliance experts.
Tags:
Cybersecurity
October 24, 2018

Comments