This article first appeared on 1776dc.com on January 7th, 2014.


(Photo courtesy of Flickr / USDA)
I typically can tell if a health-tech startup complies with the law within the first few minutes of a conversation with an entrepreneur. In fact, he or she often gives it away in the first statement—one that usually is intended to persuade me they comply with the Health Insurance Portability and Accountability Act.
The objective of HIPAA is to protect the “confidentiality, integrity and security” of electronic medical data, but data storage is just one part of it. The HIPAA security rule alone comprises 42 standards and implementation specifications spread across 3 groups—administrative, physical, and technical. Equally important is determining who has access to the data; how and where the data is being shared; and who can edit or delete the data.
The sheer complication of HIPAA makes it a minefield, especially for young startups and entrepreneurs. For example, the phrases, “We are HIPAA compliant because we use a HIPAA-compliant data center,” or, “We store our data on Amazon and have a Business Associates Agreement in place,” signal trouble. As a result, my conversations with these entrepreneurs often shift; rather than try to persuade me they are HIPAA compliant, they become exasperated, saying, “But we are just a startup, what more are we expected to do?”
Unfortunately, the determination of whether or not HIPAA applies is not based on company size or resources. Rather, it is solely dependent on whether the company is handling protected data on behalf of a Covered Entity. Given the recent changes in the law, which mean that Business Associates are now federally liable under HIPAA, the regulations are a huge issue for any young organization looking to operate in the health domain.
Still, many health tech startups turn a blind eye toward HIPAA—or simply ignore the reality of the situation in order to focus on building their business. However, as one who has conducted multiple security audits, including one based directly on the Office of Civil Rights HIPAA audit protocols, I know firsthand that ignoring HIPAA is taking a huge and unnecessary risk.
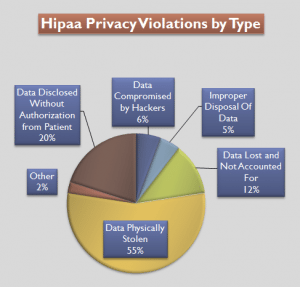
Based on data available from The U.S Department of Health and Human Services for the period 9/22/2009 to 07/04/2012. (Image courtesy of Compliance and Safety LLC)
Here are 4 key reasons why not having a robust, HIPAA-compliant framework in place can come back and bust you.
1. The Office of Civil Rights (OCR) has the power to audit any covered entity or business associate at any time. While the size and scope of an organization plays a determining role in any penalty, the issue of compliance or non-compliance is typically black or white. Admittedly the chances of OCR randomly choosing to audit a small health tech startup are remote, but it is not impossible.
2. If a data breach occurs then a company is obliged under HIPAA to report it—and that’s when compliance is crucial. Any company that suffers a data breach will be on OCR’s radar, regardless of the size of the company or of the breach. Earlier this year the Department of Health and Human Services announced the first HIPAA breach settlement involving less than 500 records with the Hospice of North Idaho, which agreed to pay $50,000 to settle violations after an unencrypted laptop containing just 441 patient records was stolen. And this is a minor case; fines can be, and usually are, much larger, reaching up to $1.5 million per breach type. (And as if that’s not enough, all companies found guilty of a breach are listed for public humiliation on the OCR website.)
3. More commonly, the lack of a HIPAA-compliant framework becomes an issue when the company tries to secure a contract with a larger, more established organization such as a health plan, pharmaceutical company or provider network. These corporations must comply with strict HIPAA requirements; they are required to conduct a due diligence audit on any supplier they may entrust with ePHI. Failure to ensure the supplier has adequate protections in place would make them liable. And typically these audits occur at the 11th hour, just when the contract is due to be signed. Not only can this delay a deal, but also can scupper it altogether depending whether or not a company can remediate in time.
4. Finally, while seed or angel investors rarely conduct due diligence at this level, it is certain that for a Series-A round and beyond any institutional investor will want to know what level of risk they are taking on. These issues also have a similar tendency to spring up toward the end of a negotiation and become a significant obstacle to closing the deal—and since a component of demonstrating compliance is providing past evidence, this is not often something that can be done retrospectively. As with many things, though, compliance is a journey, not a destination.
Companies need not read this and then drop everything to focus on HIPAA compliance. The important thing to do is take the first steps, recognizing that an inadequate compliance program is better than none at all. Seek support to have a risk assessment conducted. This does not need to be expensive but you will likely need the support of a third party to conduct it. Then, put a governance model in place and designate a team member to be responsible for compliance; that alone will satisfy at least one HIPAA requirement. Finally, start developing polices now. Even a simple, three-line policy is better than none at all.
Compliance does not need to be your number one priority—but it should be at least among the top five. With the right guidance and support, you can soon start telling people like me, “We have a robust information security framework in place that underpins your HIPAA compliance program.” That way I will need to conduct the risk assessment to know how compliant you really are.
Grant Elliott is the founder and CEO of Ostendio, a cloud-based security compliance company and a 1776 member.

January 7, 2014

Comments